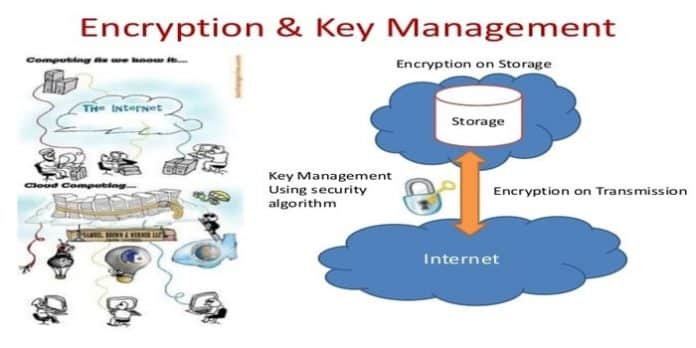
Cloud Encryption Algorithm is a component of data transport security. This Algorithm is nothing but some sequence of mathematics. This algorithm varying block ciphers to encrypt electronic 0 and 1.
Encryption algorithms stop data fraud, such as that perpetrated by bad persons who unlawfully obtain electronic information. This Encryption Algorithm is found in software applications and a part of any company’s risk management protocols.
Encryption algorithms help in transforming plain text into encrypted text and again reverse to plain text for the tenacity of securing cloud data when it is transported over networks. You can use Cloud OS for this.
Cloud Encryption Algorithm
Encryption algorithms are frequently used in cloud communications, with FTP transfers. Generally, algorithms are used to deliver secure transfers. When a cloud encryption algorithm is used in data transfer, the file at first translated into apparently worthless encryption text and then transferred in this formation; the receiving computer uses a key to interpret the cipher into its unique form. So if the message or file is captured before it reaches the receiving computer it is in an ineffectual (or encrypted) form.
When cloud data is encrypted through Cloud Encryption Algorithm data becomes more secure, accurate and safe from bad persons for any fraudulent activities. If the bad persons become more mathematical then the issue is more sophisticated.
Encryption algorithms may vary in size, but the power of an algorithm is usually directly proportional to its size. First Encryption Algorithm was developed by U.S. mathematicians Ron Rivest, Adi Shamir, and Len Adleman in the year 1977.
How Cloud Encryption Algorithm Works
Cloud Encryption Algorithm is an exciting piece of technology that works by scrambling information so it is incomprehensible by bad persons. We can show it as an example:
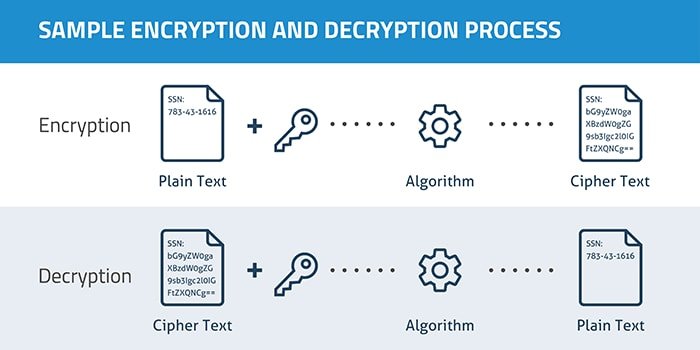
Suppose I want to transfer an encrypted message like “Darling, we will meet 30 February afternoon in your empty house”. The message will be converted like:
wUwLOnkBAf4vxSpQgQZltcz7LWwEquhdm5kSQIkQlZtfxtSTsmaw q6gVH8SimlChL2FdgvdIC7sDv7G1Z7pCNzFLp0lgB9ACm8r5RZOBi N5ske9cBVjlVfgmQ9VpFzSwzLLODhCUrW3NGQZfz3SSWviwCe7G=PAb3
When my text is encrypted normally it becomes a jumbled character and equipped with the secret passcode and will be decoded in a reverse way.
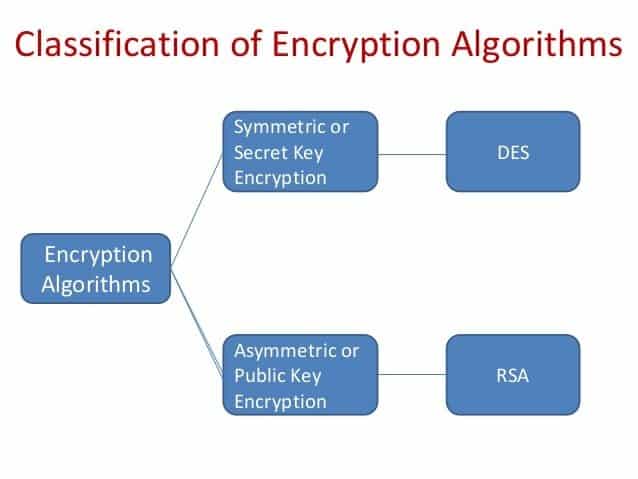
Blowfish (cipher) Encryption Algorithm
The Encryption Algorithm Blowfish is a symmetric-key block cipher. It was developed in 1993 by Bruce Schneier. This algorithm a big number of cipher suites and encryption goods.
- Designers: Bruce Schneier
- First published: 1993
- Successors: Twofish
Cipher detail
- Key sizes:32–448 bits
- Block sizes: 64 bits
- Structure: Feistel network
- Rounds: 16
AES Encryption Algorithm
The Advanced Encryption Standard (AES), also famous by its original name Rijndael, is a requirement for the encryption of electronic data recognized by the United States National Institute of Standards and Technology in 2001. This Cloud Encryption Algorithm is also widely used.
- Designers: Vincent Rijmen, Joan Daemen
- First published: 1998
- Derived from: Square
- Successors: Anubis, Grand Cru
- Certification: AES winner, CRYPTREC, NESSIE, NSA
- Key sizes: 128, 192 or 256 bits[note 1]
- Block sizes: 128 bits[note 2]
- Structure: Substitution–permutation network
- Rounds: 10, 12 or 14 (depending on the key size)
Twofish Encryption Algorithm
Twofish Cloud Encryption Algorithm is a symmetric key block cipher with a block size of 128 bits and key dimensions up to 256 bits. It was one of the five qualifiers of the Advanced Encryption Standard contest, but it was not nominated for standardization.
- Designers Bruce Schneier
- First published 1998
- Derived from Blowfish, SAFER, Square
- Related to Threefish
- Certification AES finalist
Cipher detail
- Key sizes 128, 192 or 256 bits
- Block sizes 128 bits
- Structure Feistel network
- Rounds 16
IDEA Encryption Algorithm
The International Data Encryption Algorithm initially is called Improved Proposed Encryption Standard. It is a symmetric-key block cipher developed by James Massey of ETH Zurich and Xuejia Lai and was first defined in 1991.
- Designers Xuejia Lai and James Massey
- Derived from PES
- Successors MMB, MESH, Akelarre,
- IDEA NXT (FOX)
Cipher detail
- Key sizes 128 bits
- Block sizes 64 bits
- Structure Lai-Massey scheme
- Rounds 5
MD5
MD5 is a message-digest algorithm is extensively used confusion function producing a 128-bit confusion value. Although MD5 was originally developed to use as a cryptographic hash function, it has been found to suffer from far-reaching susceptibilities.
- Designers Ronald Rivest
- First published in April 1992
- Series MD2, MD4, MD5, MD6
Cipher detail
- Digest sizes 128 bit
- Block sizes 512 bit
- Structure Merkle–Damgård construction
- Rounds 4
SHA 1
SHA-1 means Secure Hash Algorithm 1. SHA-1 is a cryptographic hash function that receipts an input and yields a 160-bit (20-byte) hash value known as a message digest – naturally extracted as a hexadecimal number, 40 digits size. This Cloud Encryption Algorithm is developed by the US National Security Agency and is a U.S. Federal Information Processing Standard.
- Designers National Security Agency
- First published 1993 (SHA-0),
- 1995 (SHA-1)
- Series (SHA-0), SHA-1, SHA-2, SHA-3
- Certification FIPS PUB 180-4, CRYPTREC (Monitored)
Cipher detail
- Digest sizes 160 bits
- Block sizes 512 bits
- Structure Merkle–Damgård construction
- Rounds 80
HMAC
The Cloud Encryption Algorithm HMAC is a specific type of message authentication code (MAC) including a cryptographic hash function and an undisclosed cryptographic key.
RSA Security Encryption Algorithm
The RSA algorithm is Rivest-Shamir-Adleman. RSA is widely used for securing sensitive information, mainly when being sent over an unconfident network such as the Internet.
- Designers Ron Rivest, Adi Shamir, and Leonard Adleman
- First published 1977
- Certification PKCS#1, ANSI X9.31, IEEE 1363
Cipher detail
- Key sizes 1,024 to 4,096 bit typical
- Rounds 1
Advantages
- Encryption Provides Security for Data
- Encrypted Data Preserves Integrity
- The Encryption Protects Privacy
- Encryption is Part of Compliance
- Encryption Protects Data across Devices
- Peace of Mind of satisfaction
- Identity Theft Protection
- Safe Decommissioning of Computer
- Unauthorized Access Protection
- Compliance with Data Protection Acts
Drawbacks/Disadvantages
- Cloud Encryption Algorithm is a very multifaceted technology.
- Running of encryption keys must be an added administrative job for often overloaded IT staff.
- Another disadvantage of encryption as it narrates to keys is that the security of data becomes the security of the encryption key.
- Lose that key, and you effectively lose your data.
- traditional full-disk encryption solutions are the reduction of overall system performance upon deployment.
Recommended: Everything You Need To Know About Cloud Internet Security and Its Threats.
Final Words
Cloud Encryption Algorithm is essential for cloud computing. So far we have discussed various types of algorithms, advantages, and disadvantages. In the sequence of our writing, we are eagerly waiting for feedback. The diversity of our knowledge is also increasing. It would be nice enough if you comment on us regarding the site.