The cloud security algorithm is a set of rules and procedures that follow to transmit data. Similarly, the process cloud computing data server follows is Security Algorithm. The cloud security algorithm denotes a wide range of strategies and policies.
It is also framed to provide controls to protect data applications. Most institutions have shifted their business information to cloud service from traditional data storage.
There are many security concerns of cloud applications and processes. That is the algorithm. An algorithm is an operating procedure. Therefore it is a set of rules, policies, strategies, procedures, and working processes. As a result, it continues the service.
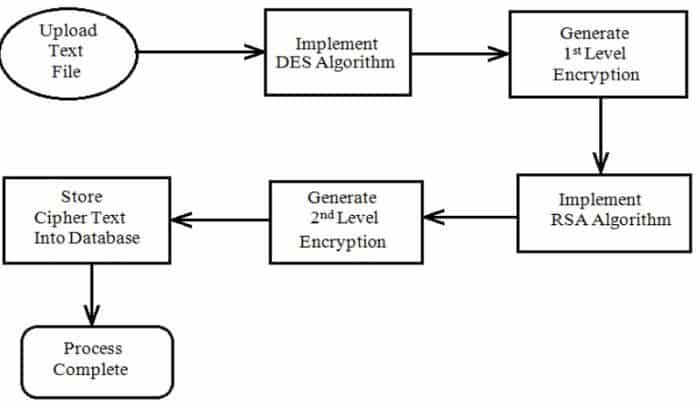
Cloud-based security providers have developed a cloud-based security algorithm to ensure that customers’ information and data are secure. The most vital feature of cloud-based security is to ensure that only legal people access the cloud.
The duty of securing the cloud lies on both the customer and the cloud service provider. Cloud customer has some specific duty to use cloud data. Besides the vendors roll customer have some responsibility to protect own data.
The requirement of Cloud-Based Security Algorithm
The cloud service provider must ensure the safety of the customer’s database. The customer will ensure the proper utilization of the application software. Cloud-based applications are suitable for many businesses.
Cloud services permit a customer to get data in real-time. So they allow secure data management, analysis, and access from every place. Cloud creates a platform for the organization to work off-premises.
Likewise, there are some risk factors hijacking accounts, data breaches, unauthorized access, and abuse of data by employees. Therefore Cloud-Based Security Algorithm developed a strategy to secure data. Some algorithms are:
1. Secure the Server
A normal server has fewer tools to check security systems. As a result, the servers have to protect themselves from external threats. On the other hand, the cloud server gets a request from the cloud. So we can route the traffic, first of all, the cloud analysis the traffic. Finally, it provides access.
2. Inspects and Filters Data
The average server has applications that filter data. If all is correct, then it reaches the server. The applications are costly and difficult to maintain. They filter web traffic afterward it reaches its network.
Sometimes the server computer gets overwhelmed and needs to shut down to block the traffic. As a result, they do not serve the intended functions. In contrast, cloud web security service filters the data and accept.
3. Private Cloud
Some organization has a private cloud. A private cloud is more secure than a shared cloud. It isolates the user from unwanted access. This option can be a good option for a cloud lover.
4. Secure Encryption and Data Management
Encryption systems use complex algorithms to protect and conceal data. Cloud-based security identity of data and limits access from bad applications that could decrypt the encrypted files.
Compliance of Cloud Security Algorithm
The cloud security algorithm has set compliance instructions to be firmly followed to safeguard the database’s safety. Cloud service providers are bound by laws and regulations. So they uphold high standards of privacy and protection of the client’s data.
Besides the Cloud Security Algorithm, there should have a Cloud user Security Algorithm. User security algorithm means the rules and procedures which the user should follow to protect their data.
It is not the only duty of the vendor to keep your data secret. It would help if you controlled the flow of your data. So you should authorize your data usage. Develop a mechanism not to login data outside the office premises. The user security algorithm is:
1. Service Level Agreement
In any hosting, a service level agreement is a must. It is the rules and regulations which follow by both parties. Since SLA is critical, then every customer must read it. It is the constitution in which both parties will follow this. Many cloud service providers made a trap using a service level agreement. So the customer should read between the lines.
In service level agreement main issue is data migration from a present vendor to another vendor. Who will take the backup? That is the question? Is payment at the beginning of a month or in advance? Can the cloud service provider control the data? Where is the location of the data center? Who will synchronize the data? That’s are the common question of service level agreement.
2. Avoid Public WiFi
As a user of the cloud service, you should be careful. You do not connect your device to public WiFi networks or any hotspot. Because it may steal your data passing through public WiFi networks, an unauthorized person can access your Cloud Security Algorithm.
If your device is connected with the cloud server and you use it through public WiFi network, your data may lose. Anytime data manipulation may occur. Do not allow your employees to use cloud computing services outside the office premises. They may play with data as well as with you. So you may use your virtual router.
3. Install and Update OS
Cloud operating system is a type of regular operating system. Cloud OS is used for transmitting data to a cloud. It manages operations, execution, and process with the virtual machine, virtual server, and virtual environment.
Cloud OS is known as a virtual OS. This OS is nothing but an application to connect with the cloud. So Cloud OS manage thread and filter request to the cloud. As a user, you have to implement cloud OS before going cloud. Proper knowledge of cloud OS is just like a cloud user.
4. Anti-malware Program
It is mandatory to use a cloud-based malware program on your PC. There is a lot of cloud antivirus software. You can use some of them for free. Paid antivirus software is also available. This cloud antivirus will save your data because they filter any request. As a result, malware cannot get admitted.
5. Do Not Share Personal Info/Device
Sharing personal devices or gadgets is a curse. By a single share, your data may send to another hand. Any spyware can be installed in a few seconds. If so, all data will be passing in the blink of an eye. Cloud cannot ensure your privacy if you cannot save yourself. Sharing personal data is also a curse. So be aware of using unauthorized applications.
6. Avoid Financial Data
Cloud is good. But storing all types of information on the cloud is not good. Wrong persons are waiting for your cloud data. The employee of the cloud service provider may also have an interest in your data. So most financial organizations do not go for cloud operation. As a result of only 10% of the real world, data is IN ON CLOUD.
7. Two Factor Applications
Two-factor protection means protecting data with a password and by any other means. The other factors may be short message service (SMS) verification, secondary mail, dongle, voice call, etc. The wrong persons can destroy your password but capturing mobile is almost impossible.
8. Privacy
Use a robust privacy model for your organization. Make an audit trail. Segregate the duty. Authorize who is for what? Restrict the employee from using your application from outside the organization. Stop using an application on mobile. Make a firm privacy policy. Force all to use your discipline. Most of the threat of any organization comes from its employee because they know everything about your company.
Final Words
Cloud Security Algorithm is a vast issue. By maintaining the issue, you may become safe. However, you may not always be well conversant regarding the knowledge of this algorithm. This will inspire your passion for clouding computing.





