Instagram has become one of the most popular social networking sites nowadays. People from different countries of the world use this social media platform. They share their photos along with various captions with others using this. It is also a chatting platform. You might use your Instagram account thinking that it is secured. But what if you fall victim to Instagram phishing? You should have basic knowledge regarding this important matter.
What is Instagram Phishing?
If someone wants to steal your Instagram identity, phishing can be an easier way for him. It is a standard method of hacking one’s Instagram account. Most of the hackers are using this technique to collect information from other peoples’ accounts. They can hand over your information to any third parties by this process. They can do this job even creating no doubt for you!
The hackers create a spoofed Instagram page to befool you. It will require your personal information through sharing a link or message. The hackers might also steal information from you by making you feel nervous. They threaten to delete your account if you refuse to give the required information. In most cases, people feel insecure and give all the information to them. As a result, the hackers get control over their Instagram accounts.
Types of Phishing
Hackers usually use four types of phishing methods. These techniques help them gain access to your account. Those methods are-
- Spear Phishing: Using this method, the hackers mainly target to get control over the Instagram account of an individual. They send a spear-phishing email containing a link. The email convinces the users to download the link. When someone clicks it, his information gets transferred to the hackers.
- Whaling: They use this process when the hackers target to hack the account of a business company. Informative emails are sent to the CEO, CFO, or other leading members providing separate links. The email says that the link contains more information about a specific matter. And by clicking that link, the user delivers his information to the hackers.
- Vishing: In the vishing method, the hacker calls the user, addressing himself as a Microsoft representative. He tells the user about finding a virus on the computer. The scammer requires the user’s credit card details. He assures the user of installing the updated version of the anti-virus. Now, the hacker can easily control all your information.
- Email Phishing: The hacker sends emails to the users, requiring them to log in to their accounts. Most of the users click the link to log in to their accounts. It causes information theft.

These phishing methods are used to collect data. The phishers use these techniques on people’s Instagram accounts. These are used to collect data from other social networking sites, too.
Causes of Instagram Phishing
The demand for Instagram is increasing day by day throughout the world. Now, the phishers are taking the chance to collect the personal Infos of the users illegally. There are many reasons for getting your Instagram account hacked. But mostly, the phishers do this for the following causes-
- For stealing your Instagram identity.
- To collect your personal information.
- For spreading false information about yourself.
- To get access to your bank account.
- For getting control over your other social media accounts.
- To demand money or other things for giving your account back.
From the users’ point of view, some reasons are also mentionable. Lack of cautiousness is one of the most important reasons for Instagram spoofing. Over-excitement also paves this may. It happens when you follow the instructions asked by the scammers immediately. If you can control your excitement and handle the situation calmly, it reduces the risk.
Among the other reasons, setting a weak password is one. Again, you might use some third-party apps for your Instagram account. These accounts require access to your profile. It is another reason for beige your information exposed. Always be careful about the activities in your account. If something fishy knocks your mind, immediately inform the Instagram authority. But of course, via email.
If you fall victim to Instagram scamming, the intentions of the phishers will be successful. So, isn’t it better to use your account more carefully? Of course, yes!
Instagram Phishing Email
The Instagram scamming email has become the most common method of spoofing. Here, the phishers send emails to the users using the logo of Instagram. The email informs them that your account has been hacked. It may also accuse them of copyright violations. After getting such kinds of emails, it is pretty normal for the users to be confused.
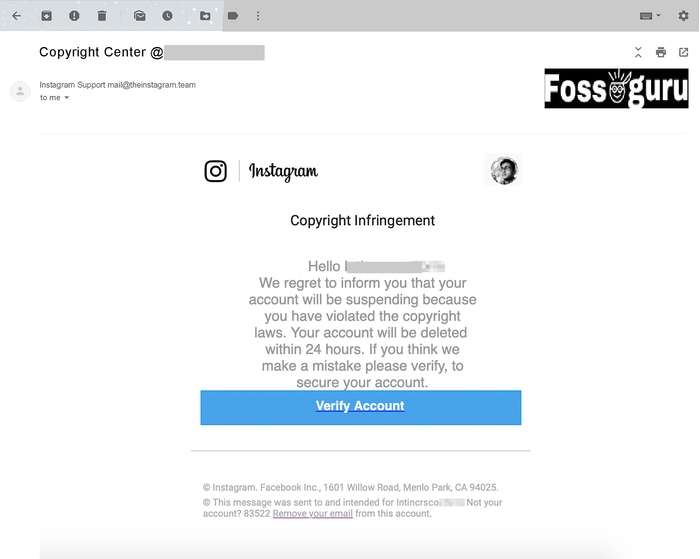
These emails contain a separate link. They require the users to click the link and log in to their accounts. And this is what the phishers want. When you use your email and password to log in, they have already trapped you on their network. So, it is better to assume these kinds of emails as scams. Rechecking the security provisions of Instagram may help you.
Instagram Scamming Message
The phishers also use the direct message method to hack your Instagram ID. The phishers address themselves as the representative of the Instagram support center. They send you suspicious messages about your Instagram account. It is challenging to assume such kinds of statements as spam. They have trapped many celebrities and social figures all over the world in this method.
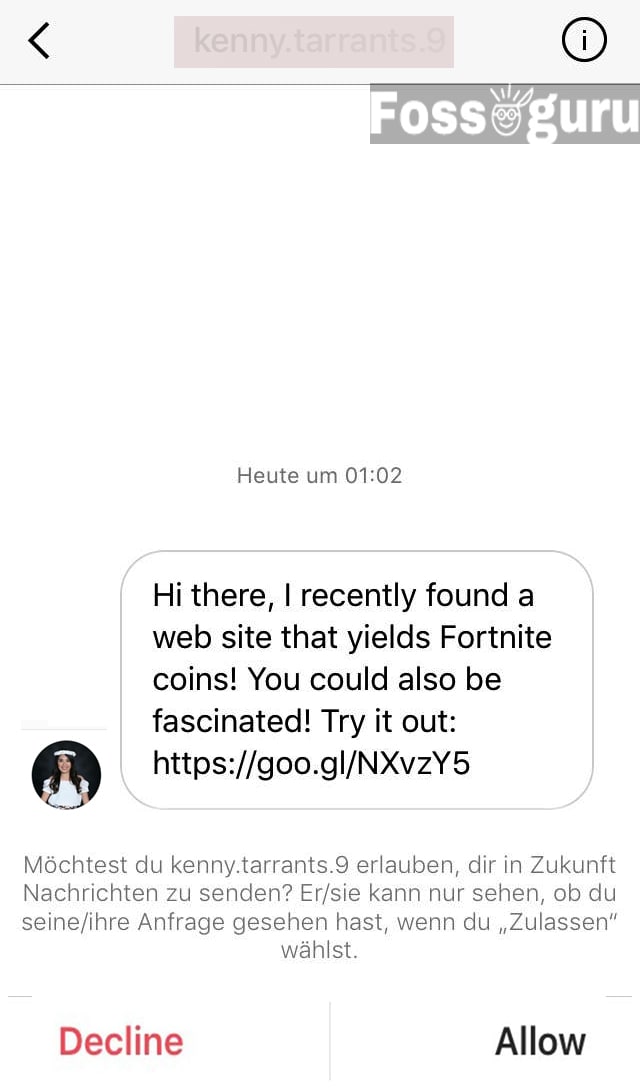
Instagram phishing messages, most of the time, accuses you of copyright violation. It might also tell you that someone has hacked your account. Also, you can get an offer to earn a verified badge by clicking the link. Being excited after getting these messages, people click the link immediately. As a result, they lost control over their account. They can lock the accounts out of Instagram.
There are several cases where the users couldn’t even realize that someone had hacked their account. Usually, the phishers use the hacked Instagram accounts to spread false news about the users. Now, it became more accessible after adding the message-deleting option. The scammers send direct messages to other people pretending to be the user. Sometimes, they describe imaginary emergencies to them and demand money. And after that, they remove the message from the chatbox. So, there is no chance to doubt any suspicious activities.
Instagram Security Email Scam
Instagram has added an option to help you to figure out the spam emails. If you get an email from the Instagram support center, don’t be over sure about its relevance. The phishers use your overconfidence to trap you. You should handle it with a relaxed mind. And Instagram authority has shown a way to identify that.
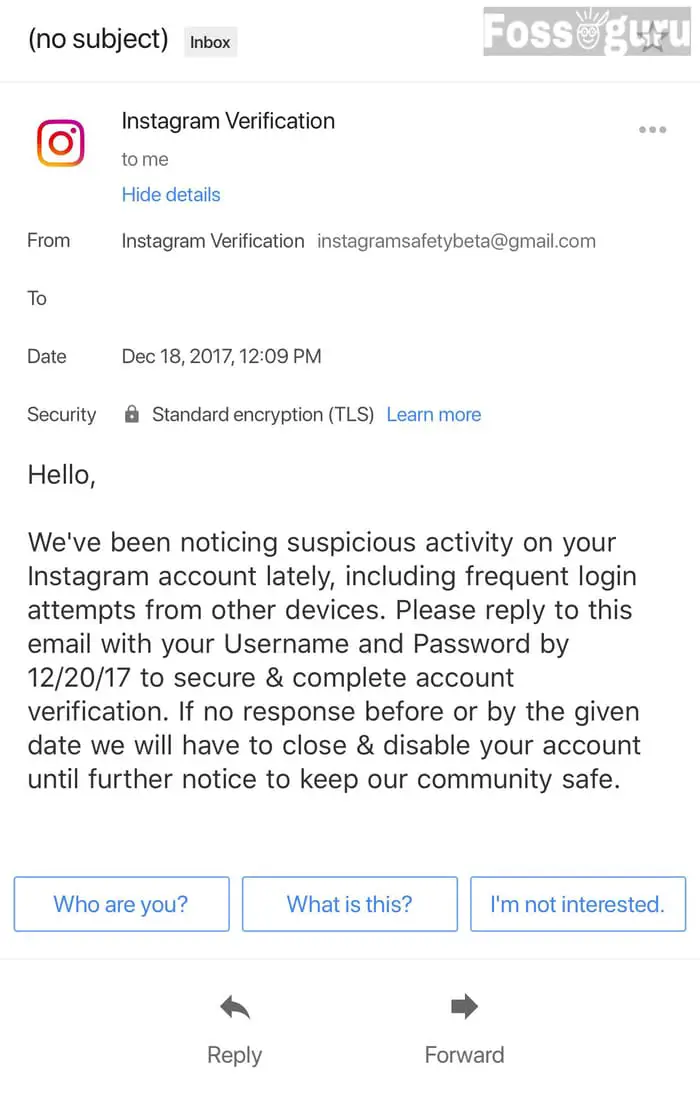
The Instagram authority stores the emails they have sent to you within the last 14 days. To recheck the mails, you have to follow some steps-
- First, open your Instagram account.
- Then tap into your profile picture to visit your profile.
- After that, tap the settings option.
- Find out the security button.
- Then select the ‘emails from Instagram’ option.
If you get a scammed email, it will not be present in this option. Here is another vital piece of information for you. The official emails from Instagram do not address you by your name. And they will never send you direct messages.
Instagram Login Scams
Instagram phishers are using another technique to hack the account. They are using the login scams to befool the users. This scam is pretty much hard to identify as a fake one. The phishers targeted the conscious users to fall on the trap created by their consciousness. Don’t be confused. I’m making it clear to you.
Instagram login scams are like the 2-factor authentication feature. Most of the users know about this feature of Instagram. So, when they get an email from the authority requiring them to confirm their identity, they do not think it is fake. The hackers take help from modern engineering techniques. They have designed a message that looks like a genuine message from the authority. This warning message makes the scam more believable to them.
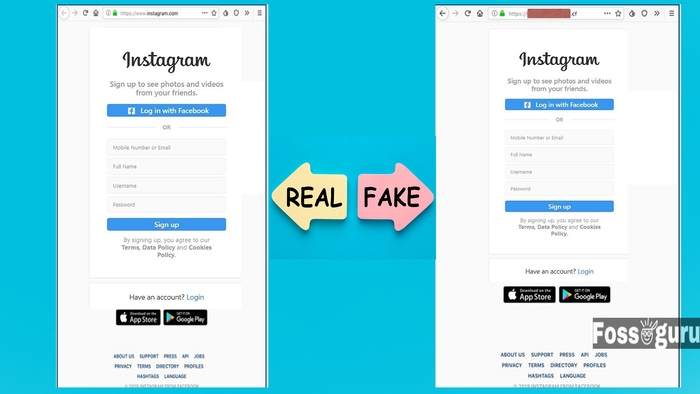
The phishers create a fake page similar to any user’s Instagram account. They alert that someone is trying to log in to his account. The email convinces the user to log in to the link provided to ensure his identity. Then they send that link to the user. Through this process, the phishers get all the information from his account.
This scam also included a code verification option. But it is made to ensure that you have received the scam email. Apart from some grammatical mistakes, these scam emails can barely differentiate from the real ones. However, the phishers do not use the ‘instagram.com’ domain while sending such emails. Their domain name is ‘.CF’. If you remain careful on this point, you can avoid login scams.
Examples of Instagram Scamming Websites
As I mentioned before, there are mainly four types of phishing methods. Smishing, clone phishing, evil twin phishing, search engine phishing, pharming, etc., are also used for phishing. The Instagram phishers use these methods differently to collect data from the users. But, phishers are discovering new ways to get stronger. Here are some examples of their phishing techniques.
Example 1: An Instagram user named Peter Slattery faced such a problem. He is an Instagram badge holder. On 15 October 2020, Peter posted he used to get many suspicious messages from the Instagram authority. The messages accused him of violation of their copyright policy. The scammers also threatened to remove his account within 24 hours if he refused to click the link and fill up the attached form.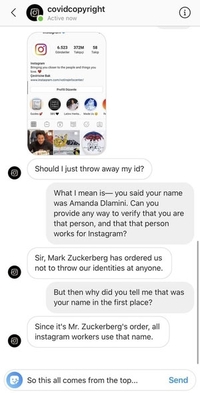
Peter immediately contacted the Instagram authority. They ensured Peter didn’t violate any copyright policy. As he had been working with Instagram for a long time, he knew about these scams. It helped him to avoid Instagram phishing.
Example 2: Bollywood actress Esha Doel got the same type of messages from scammers. It was also about violating the copyright policies. Getting worried, she clicked on the link. Eventually, her Instagram account was hacked. The phishers collected her personal information. They also spread misleading news about her.
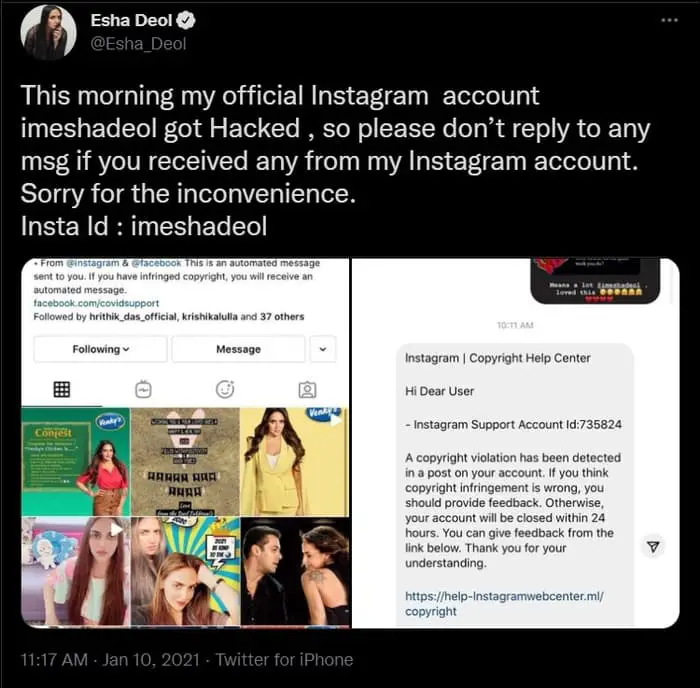
Instagram scamming has become a common incident in recent times. You can find a lot of examples like the ones I’ve mentioned. The phishers are creating spam messages flawlessly. The primary intention of the scammers is to ensure your clicking on the link. So, you should be very cautious about opening any link.
Instagram Phishing Link
The scammers attach a phishing link to the email or message. They try to convince the users to click the link. Mainly, it is a spoofed account link made by scammers. After entering the link, it is hard to find any difference between the real and the fake account. But you had already logged in to the scammed account using your email ID and password. That is the main reason for sending you the message.
But there is a slight difference between the original Instagram account link and the fake one. Always notice the domain name of the link. Here is a scammed account link-
Look carefully. The link doesn’t contain the domain name ‘Instagram.com.’ Before clicking any link, be careful about this matter. It will reduce the possibility of hacking your account.
Instagram Scamming Attack
It is popularly said that we use the term phishing as a substitute for ‘fishing.’ Like fishing in the sea, phishers take millions of Instagram users as their fishing ground. Among them, they fish out the password, email address, and other information from some specific Instagram ID holders. Here, instead of the letter ‘F,’ phishing starts with ‘ph.’ It is done to make it separate from ‘fishing.’
The Instagram scamming attack is increasing at an alarming rate. The phishers are using innovative methods to trap the users. An Instagram spoofing attack can expose all the personal information of a person. Again, hackers use the ID to gain profit. Nowadays, they are targeting verified accounts. It is easy for the phishers to gain trust from the other users while messaging others. Because people usually believe the accounts that hold a blue tick, taking those as accurate. As a result, the scammers can easily earn money from them.
Some common matters are present on a message used to phish Instagram. These elements are called the ‘Red Flag’ of Instagram phishing. Most phishing messages contain some common mistakes. The red flags of Instagram scamming are-
- In most cases, you might receive a message from the Instagram authority or a person. He addresses himself as a representative of Instagram.
- The scammers usually use an unfamiliar tone or addressing words at the beginning of the message or email. They might address you with your name. Or, you might get messages starting with the phrase ‘Dear member.’
- Spelling or grammatical mistakes are the frequent errors of a scammed message. If you look at the message carefully, there is every chance to find such mistakes. Even mistakes are prevalent in the links provided by the scammers.
- The phishers usually want to ensure you’re clicking on the link rapidly because they would get what they want. So, the language used in the message expresses the urgency. They try to convince you at any cost to click the link within the shortest period.
- You may find threatening words in the scammed messages. The scammers might threaten you to delete your account if you do not follow their instructions. Even they might give you a time limit of 24 hours.
- There might be login scams informing you about someone’s illegal entry into your account. And being panicked, most of the users click the link. The link requires the email address and password. After logging in with that scammed link, the user eventually hands over the information to the scammer.
- The messages that demand money or any other financial help are generally treated as fake. When the scammers get control over the account of any user, they usually send these kinds of messages to others to earn profit.
- The major sign of a scammed message is it contains a link. This link is the power bank of the phishers. If they cannot convince you to click it, their attempts will go in vain.
If you get an email or direct message from anyone pretending to be the Instagram authority, just check out these points. Make sure that you are not giving any chances to the phishers to steal your account.
How to Prevent Instagram Phishing Attacks?
It is normal to get nervous, knowing the increasing amounts of Instagram scamming cases. Who wants to expose his private information to the outside world? Instagram spoofing is indeed a heinous cybercrime. It violates one’s privacy. Moreover, the scammers use illegal tricks to collect information from the targeted users. It causes great harm to the user and his near ones as well. Sometimes, the scammers do such notorious acts to defame a person. It destroys his career and lifestyle.
The growing rate of phishing leads cyber researchers to find out ways to prevent them. You need to know the methods of avoiding Instagram scamming. Otherwise, you cannot claim yourself as a safe Instagram user. Who knows, you are not the next victim of phishing? Though there are no full-fledged preventive methods available to stop this problem, you must try. By following some steps, you can reduce the chances of getting your account hacked. Here is a list of the phishing preventive measures-
1. Be careful about permitting apps
We all know that many third-party apps require permissions to access your device. You must be careful about allowing an app to access your information. It includes your gallery, location, contacts, and so on. You might use an app to save your Instagram photos.
But there is a chance of leaking your information through this. These kinds of apps require access to your Instagram account. Log in to the app using your email ID and password. If there is an ill intention behind that, your Infos can be exposed.
2. Turn on the 2 step verification feature
Instagram has added a two-step verification feature to ensure your account safety. It prevents illegal trespass into your Instagram account. This feature requires your email address and phone number. It will notify you if someone tries to enter your account.
When you try to log in to your account using another device, the Instagram authority will send a verification code on your phone. So, you can quickly get a notification if someone does so. Again, without the verification code, it is hard to access your Instagram account.
3. Avoid using Bots
A bot is a short form of robot used in the cyber field. You might get offers for increasing the number of your Instagram followers automatically. Besides, they also offer to provide you with automated comments and likes on your posts. To become an Instagram celebrity, many of the users fall into this trap.
These types of bots can collect your Instagram information. They can access your account. A lot of business pages use this method to increase their followers. But by doing so, they push their account towards the risk of cyber phishing.
4. Stay conscious about downloading apps
If you want to use any side app for Instagram, do not install random apps. The editor’s choice apps are pretty reliable. You can download those. But don’t be flattered by seeing the high review rate. These reviews might be fake too!
5. Avoid login Links
If any message instructs you to log in to your account using the provided link, assume it is a scam. Always log in to your account through the official.
6. Set different strong passwords for individual apps
It is wise to set different passwords for the apps. Some apps are linked up with others. Putting the same password for all the apps may lead you to get all your accounts hacked together.
Always try to set a unique password. Your password should contain letters, numbers, and special characters. It prevents the phishers from guessing your password easily.
7. Be aware of the Phishing red flags
After getting any unusual message, check it carefully. If you find any symptoms of being a fake one, avoid it. You can also contact the Instagram authority to ensure its relevance.
8. Don’t panic
Getting panicked or excited can lead you to the wrong path. So, keep yourself relaxed after getting a threatening message or an exciting offer. You have to think twice before going for it. First, check the content of the message. Try to find out any irregularities. Handling situations in a relaxed mind can prevent a lot of upcoming dangers.
These matters are undoubtedly essential to prevent your account-related issues. Use your Instagram account following many precautions. It will keep you protected from any unwanted risks.
Types of Phishing Attacks
Scammers can make Instagram phishing attacks using a lot of techniques. Any suspicious activity of your Instagram account may be a symptom of the spam attack. In such a case, you cannot even imagine that your account is being controlled by someone else too! The phishers can do these activities keeping no trace too.
Generally, phishers use two common methods to collect data from the users’ accounts. The methods are-
- Ninja Mode
- Owning Mode
The ninja mode may be termed as the co-sharing mode. Here, the phisher takes control of your account. But he doesn’t want to expose this to you. He stays as a shadow user. The phisher then logs into your account and keeps tracking your daily activities. He might use the direct message option to gain more information from others. Using the ‘un-sent message’ option, he can delete the evidence. In this way, they can expose your private account to phishers. But you remain unaware about the whole thing!
The owning mode signifies the hacker is the present owner of your account. He lets you know about this matter by doing some acts. He may delete your previous posts. Sometimes, the hackers change the username of the ID! If your account contains a lot of followers, the hackers might sell it to others. In such cases, it will lock your Instagram account for phishing.
There are some other types of Instagram spoofing attacks used by hackers. The frequently used techniques are-
- Offering you a lottery: You might get a message of winning a lottery. The hackers send you such directives to make you excited. They provoke you to click the link to know the details. They might even offer you to pay fees for clicking the link. And if you somehow click it, it will transfer your account information to them.
- Building up a romantic relationship: Some phishers use the emotion of the users to achieve their goals. When a user trusts him, the phisher takes out the secret information from her. Such a hacker creates emotional bonding with the users. Even the user may turn into a victim of blackmailing if she refuses to share the info.
- Sending Instagram scamming emails and messages: The hackers might send you scammed messages or emails containing false info. They pretend to be the Instagram authority. This kind of message informs you about your account safety. Or it might accuse you of violating any policies on Instagram.
- Making Clone Phishing: Hackers can create a doppelganger account of your real one! There is no chance for the outsiders. The primary intention of creating a clone account is to go closer to your near ones. The hacker claims it is your new account. He tries to collect info about you. Taking the help of your friends and family, the hacker can reach his goal.
- Verification Badge Scam: Some hackers might offer to convert your account into a verified one. For this, they invoke you to click the link they have provided. Falling on the trap, you may lose your account.
These are the common tricks that phishers use. But you can find many more examples around you. They are discovering lots of new methods to trap you. However, you can avoid these kinds of trap phishing by staying conscious. A single bit of unawareness may cause severe destruction.
Identifying the Instagram Phishing Attacks
I have already discussed the techniques of identifying the Instagram scamming attacks. Some simple tricks may help you to realize that you are going to fall into a trap. Now I’m summarizing the tips-
- Check the domain name of the link. The fake links do not contain the ‘Instagram.com’ domain name.
- Mark it as spam if someone sends you a direct message claiming to be the Instagram authority.
- Recheck the grammatical and spelling errors of the message or email.
- Ensure the relevance of the messages claiming money.
- Contact the Instagram support team if the message claims any policy violation issues.
If you find these sorts of irregularities in any messages or emails, try to avoid them. Usually, these tricks are used to identify a spoofing attack.
Top 10 Solutions After an Instagram Phishing Attack
I’ve much discussed the preventive measures of Instagram scamming attacks. However, you may do it accidentally. But you might still get your account hacked. Or you might click on the phishing link after getting panicked. But when you realize that you have done something wrong, it may cause great tension between you.
We all know the wise saying, ‘To err is human, to forgive is divine.’ It is pretty normal to make some mistakes. So, instead of blaming yourself, try to find out the ways to recover your account. The Instagram authority has made some features to help you in this situation. Having any doubt about hacking, you can take help from the authorities.
The rate of spoofing is enlarging. As a result, the users are demanding some effective strong preventions. Side by side, they have claimed more ways to recover their hacked accounts. To solve these issues, the Instagram authority has been researching new ways to beat the phishers. You can term these ways as the solutions after Instagram scamming attacks. Now, I’m describing the best ten solutions for spoofing attacks. You may follow these measures after being a victim of Instagram spoofing.
1. Changing Password
If someone uses your account illegally, you can quickly identify it. You might find inappropriate posts and comments on your account. Moreover, the phisher might use your identity to spread false information. Your Instagram account represents your identity. If a third party handles your account, it is a dangerous matter. You have to take immediate steps after realizing this phishing.
Here, Instagram suggests you change your password. This method is applicable when the phisher uses your account without changing your info. You have to go to the settings option and reset your password. You can send a ‘password reset email’ to yourself to verify your identity.
2. Revoke Third-Party Access
You might be using other third-party apps that require access to your Instagram account. After changing your password, immediately revoke the access of any third-party apps to your account. These apps sometimes collect your data and expose them to others. If you still allow their entry, the phisher will probably get your new info too!
3. Check your Log In Activities
You can find out the locations where your Instagram account has been logged in. You can also know the device’s names. To get this information, you have to tap the settings option of your account. Then click ‘Login Activity.’
You can find the login history of your account here. So, whenever you doubt unauthorized access to your account, check this option. This measure will make you clear about if someone else is using your account.
4. Check Email
The Instagram authority will send you an email if there are any security issues. So, when a phisher tries to enter your account, you will get an email from [email protected]. It will inform you that someone has changed your password. You will get a revert option with the mail. By using it, you can revert to the changes made by the phisher.
5. Request to send a Login Link
Sometimes, the phishers change the additional information about your account. In that case, you cannot change your password. You have to take help from the authorities to handle this situation. You need to request the Instagram support center to send you an alternative login link. The steps are:
- Go to the login screen. Tap the ‘Get Help Logging In’ button for android devices and ‘Forgot Password’ for iOS.
- If the phisher has already changed this info, tap the ‘Need more help’ option. Type your username, email address, or phone number you set for your account. Then tap the ‘Next button.
- After following the instructions, select your email or phone number. They will send a login link to that address.
- Using this new link, you can recover your Instagram account.
6. Request for a Security Code
Are you failing to recover your account? Instagram support facilities will still help you. Following the steps below, you can make a request to the Instagram authority for sending you a security code:
For Android
If you are an android device user, you have to-
- Go to the login screen and tap the ‘Get help logging in’ option.
- Enter your Instagram username, password, phone number. Then Tap the ‘Need more help’ option.
- You have to follow the instructions they provide.
- Then select either your email or your phone number. Then tap the ‘Send security code’ option.
- You will get a six-digit security code to log in to your account.
- If you still face problems in login, tap the ‘I can’t access this email or phone number’ option. Then follow the on-screen instructions.
For iOS
If you are using an iOS device, follow these steps-
- Go to the login screen and tap the ‘Need more help’ option.
- Select your email address or phone number. Then tap the ‘Send security code’ button.
- If you don’t receive any code, tap the ‘I can’t access this email or phone number’ option. Now follow the given instructions.
7. The Username Locking Feature
Recently, Instagram has added a feature to recover the hacked account. The phishers usually target the accounts having a lot of followers. They try to sell the ID to others at a high price. For this, the phishers need to change the username of the account. Researcher Jain Manchun Wong discovered the username locking feature to prevent this crime.
When a user changes his username, it will lock the last name for the next 14 days. So, if someone wants to change the username with ill intentions, the genuine owner can have time to recover his account.
8. Identity Verification
Instagram also has an identity verification feature. When you submit a support request, the authority will verify your identity. If there are no photos of you in your account, they will ask for your other information like email, phone, device model, etc., to verify you. If they find any photos of you in the account, they will require a selfie video from you. In this way, Instagram ensures the identity of the actual account holder.
9. Turn on two Factor Authentication
If you can log in to your hacked account, immediately turn on the 2-factor authentication option. It will prevent the phisher from logging in to your account again.
10. Check the Account Centre
You must check the account Centre of Instagram to track the illegal activities. The phisher might add his other accounts’ links to your ID. Immediately remove them all. Also, check your info and change them. These steps can make your account safe again.
The Instagram support center is working great to ensure the security of its users. So, don’t be worried if you face a phishing attack. Contact the support team as early as possible. Then follow these steps accurately. Hopefully, it will help to reduce the amount of your loss.
Final Thoughts
Anyone, regardless of popularity, might be a victim of Instagram phishing. There is no alternative to self-awareness to avoid this cyber-crime. Try to use your account following all possible safety measures. And apply these techniques to prevent phishing. The Instagram authority is there for you to give the best solution.





